Setting Up Email Servers - Part 4
──────────────────────────────────────────────────────────────────────────────────
Introduction
We will be continuing our series on setting up email servers on Linux systems from Part 3. In this part, we will be configuring different types of authentication mechanisms for our email server. This one requires the Active Directory server you used in Part 1, or any identity provider in general as we will just be focusing on the email side of things. The programs we will be exploring in this guide are Postfix, Dovecot, (Microsoft AD) LDAP, Kerberos, Samba and FreeIPA.
──────────────────────────────────────────────────────────────────────────────────
Postfix - MTA
Postfix is a mail transfer agent (MTA) that is used to send and receive emails. We will be using our configuration from Part 3:
vi /etc/postfix/main.cf
myhostname = .
mydomain =
myorigin = $mydomain #$mydomain is a variable that you dont have to change.
inet_interfaces = all
mydestination = $myhostname, localhost.$mydomain, localhost, $mydomain
mynetworks = /, 127.0.0.0/8 #substitute with the networks you need to communicate with your server (typically internal RFC1918 addresses).
home_mailbox = Maildir #Maildir is what I and Dovecot choose to use by default. Mail is the traditional mailbox format.
──────────────────────────────────────────────────────────────────────────────────
Active Directory LDAP Authentication
We will be using LDAP to authenticate users against our Active Directory server. This is a common practice in enterprise environments.
Add User (on the AD Box)
net user binddn password /add /domain #for Windows ADYou might have to go into the AD Users/Groups and have this user sign in with the path @example.com
Configure
#LDAP Settings >>
vi /etc/postfix/main.cf
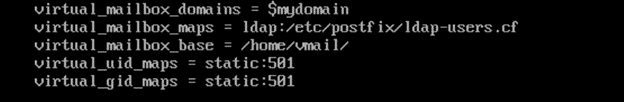
virtual_mailbox_domains = $mydomain
virtual_mailbox_base = /home/vmail/
virtual_mailbox_maps = ldap:/etc/postfix/ldap-users.cf
virtual_uid_maps = static:501
virtual_gid_maps = static:501
#Connect LDAP >>
vi /etc/postfix/ldap-users.cf
server_host = ad.example.com
search_base = dc=example,dc=com
version = 3
query_filter = (&(objectclass=person)(mail=%s))
result_attribute = samaccountname
result_format = %s/Maildir/
bind = yes
bind_dn = binddn@example.com
bind_pw = password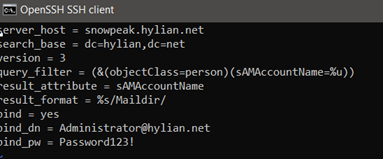
Start/Restart Postfix
postfix check && systemctl restart postfixTest Connectivity
postmap -q user@example.com ldap:/etc/postfix/ldap-users.cf #Assuming “user” exists on AD
#this should return the path to the user’s mail directory
──────────────────────────────────────────────────────────────────────────────────
Connected Authentication - FreeIPA
FreeIPA is an identity management solution that is built on top of the open-source projects like 389 Directory Server, MIT Kerberos, and SSSD. It is a great alternative to Active Directory and is a great solution for Linux environments.
Configure
- Add Service to IPA Server
- Enable Service
- Configure Basic Settings
- Integrate Postfix with Dovecot for SASL (Single Sign on for Authentication) Config
- TLS Connections
- Start / Restart Postfix
- Test Connectivity
ipa service-add smtp/www.example.comsystemctl enable postfixvi /etc/postfix/main.cf
myhostname = .
mydomain =
myorigin = $mydomain
inet_interfaces = all
mynetworks = 127.0.0.0/8, 172.16.0.0/12, 10.0.0.0/8, 192.168.0.0/16
vi /etc/postfix/master.cf
#uncomment:
submission inet n - n - - smtpd
-o syslog_name=postfix/submission
-o smtpd_tls_security_level=encrypt
-o smtpd_sasl_auth_enable=yes postconf -e ‘smtpd_sasl_type = dovecot’
postconf -e ‘smtpd_sasl_path = private/auth'
postconf -e 'smtpd_sasl_auth_enable = yes'
postconf -e ‘smtpd_relay_restrictions = permit_mynetworks, permit_sasl_authenticated, reject_unauth_destination’mkdir /etc/postfix-certs
chcon -t cert_t /etc/postfix-certs
kinit admin
ipa-getcert request -r -f /etc/postfix-certs/smtp.crt -k /etc/postfix-certs/smtp.key -N CN=webmail.example.com -D webmail.example.com -K smtp/webmail.example.com
postconf -e 'smtpd_tls_auth_only = yes'
postconf -e 'smtpd_tls_key_file = /etc/postfix-certs/smtp.key'
postconf -e 'smtpd_tls_cert_file = /etc/postfix-certs/smtp.crt'
postconf -e 'smtpd_tls_received_header = yes'
postconf -e 'smtpd_tls_session_cache_timeout = 3600s'postfix check && systemctl restart postfix#install openssl
apt-get install openssl -y
#OR
yum install openssl -y
#base64 encode username and password
echo -ne ‘\0username@example.com\0password’ | base64
openssl s_client -connect webmail.example.com:587 -starttls smtp
ehlo localhost
start tls
auth plain or login
mail from: @
rcpt to: @
data
.
quit
──────────────────────────────────────────────────────────────────────────────────
Dovecot
Dovecot is an open-source IMAP and POP3 server for Linux/UNIX-like systems, written with security primarily in mind. It is an excellent choice for both small and large installations. We will be using our configuration from Part 3:
Active Directory LDAP Authentication
Configure
vi /etc/dovecot/dovecot.conf
protocols = imap pop3 (lmtp for local mail transfer)
vi /etc/dovecot/conf.d/10-mail.conf
mail_location = maildir:~/Maildir
vi /etc/dovecot/conf.d/10-auth.conf
disable_plaintext_auth = no
auth_mechanisms = plain ntlm login
auth_username_format = %Lu
passdb {
driver = ldap
args = /etc/dovecot/conf.d/dovecot-ldap.conf
}
userdb {
driver = static
args = uid=501 gid=501 home=/home/vmail/%n
}
vi /etc/dovecot/conf.d/10-master.conf
unix_listener auth-userdb {
user = postfix
group = postfix
}
vi /etc/dovecot/conf.d/dovecot-ldap.conf
hosts = ad.example.com #or uris = ldap://ad.frog.com
base = dc=example, dc=com
ldap_version = 3
auth_bind = yes
dn = binddn
dnpass = password
auth_bind_userdn = “cn=users,dc=example,dc=com”
pass_filter = (&(objectclass=person) (uid=%u))Test
install openldap openldap-clients
ldapsearch -x -h ad.frog.com -D
──────────────────────────────────────────────────────────────────────────────────
Active Directory Kerberos Authentication
RHEL
yum -y install realmd sssd oddjob oddjob-mkhomedir adcli samba-common samba-common-tools ntpdate ntp krb5-workstationConfigure Kerberos
vi /etc/krb5.conf
[libdefaults]
default_realm = EXAMPLE.COM #all EXAMPLE.COMs must be in caps
[realms]
EXAMPLE.COM = {
kdc = ad.example.com
}
[domain_realm]
.example.com = EXAMPLE.COM
example.com = EXAMPLE.COM
.kerberos.server = EXAMPLE.COM
kinit Administrator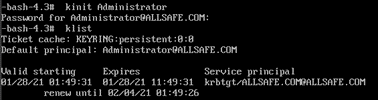
Join Box to AD Domain
realm discover ad.example.com
realm join ad.example.com
#OR
realm join -v -U administrator DOMAIN.COM --install=/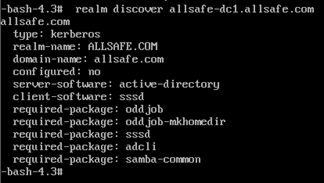
(or) via Samba
Configure
vi /etc/samba/smb.conf
[global]
workgroup = EXAMPLE
realm = EXAMPLE.COM
security = ADS
local master = no
domain master = no
preferred master = no
dns proxy = no
idmap uid = 10000-20000
idmap gid = 10000-20000
password server = ad.example.com
encrypt passwords = yes
winbind use default domain = yes
winbind separator = +Join Box to AD Domain
net ads join -U AdministratorStart Winbind Daemon
service winbind start
wbinfo -i AdministratorPAM
vi /etc/pam.d/dovecot
auth sufficient pam_krb5.so no_user_check validate
account sufficient pam_permit.soConfigure
vi /etc/dovecot/dovecot.conf
protocols = imap pop3 (lmtp for local mail transfer)
vi /etc/dovecot/conf.d/10-mail.conf
mail_location = maildir:~/Maildir
vi /etc/dovecot/conf.d/10-auth.conf
disable_plaintext_auth = no
auth_mechanisms = plain ntlm gss-spnego login
auth_use_winbind = yes
auth_winbind_helper_path = /usr/bin/ntlm_auth
auth_ntlm_use_winbind = yes #idk bout this one
userdb {
driver = static
args = uid=501 gid=501 home=/home/vmail/%n
}
vi /etc/dovecot/conf.d/10-master.conf
unix_listener auth-userdb {
#mode =0600
user = postfix
group = postfix
}
──────────────────────────────────────────────────────────────────────────────────
Connected Authentication - FreeIPA
Configure
- Add Service to IPA Server
- Add Mail Group
- Configure IPA Client
- Basic Dovecot Install
- Configure to Allow imap
- Kerberos Authentication
- Configure Mailbox Location
- Postfix SASL
- Make Mail Directory
- Generate Keytab
ipa service-add imap/www.example.comipa group-add mailusers
ipa group-add-member mailusers --users={test1,test2,test3}ref client configuration from Part 3yum -y install dovecot
systemctl enable dovecotvi /etc/dovecot/dovecot.conf
protocols = imapvi /etc/dovecot/conf.d/10-auth.conf
auth_mechanisms = plain gssapi login
auth_gssapi_hostname = webmail.example.com
auth_krb5_keytab = /etc/dovecot/krb5.keytab
auth_realms = example.com
auth_default_realm = example.com
userdb {
driver = static
args = uid=dovecot gid=dovecot home=/var/spool/mail/%u
}vi /etc/dovecot/conf.d/10-mail.conf
mail_location = mbox:/mail/%u/ : INBOX=/var/mail/%nvi /etc/dovecot/conf.d/10-master.conf
service auth {
...
unix_listener /var/spool/postfix/private/auth {
mode = 0660
# Assuming the default Postfix user and group
user = postfix
group = postfix
}mkdir /mail
chmod 770 /mail #** you might have to chmod 770 /var/mail as well
chgrp mailusers /mail
chcon -t user_home_t /mail #OR disable selinuxkinit admin
ipa-getkeytab -s ipa.example.com -p imap/webmail.example.com -k /etc/dovecot/krb5.keytab
chown root:dovecot /etc/dovecot/krb5.keytab
chmod 640 /etc/dovecot/krb5.keytab
systemctl restart dovecot
──────────────────────────────────────────────────────────────────────────────────
SSL Certs for - Roundcube HTTPS, SMTPS, POP3S, IMAPS
Roundcube
RHEL - Configuration
vi /etc/httpd/conf.d/roundcube-mail.conf
Alias /webmail /usr/share/roundcubemail
RewriteEngine on
RewriteCond %{HTTPS} !=on
RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI}
#IF YOU GET A LOG WRITE ERROR > ITS SELINUX:
(chcon -R system_u:object_r:httpd_log_t:s0 /var/log/roundcubemail
OR
semanage fcontext -a -t httpd_log_t ‘/var/log/roundcubemail(/.*)?’
restorecon -v -R /var/log/
)AND
setsebool -P httpd_can_network_connect=1FreeIPA HTTPS
yum -y install mod_ssl
mkdir /etc/httpd/httpd-certs
ipa service-add http/www.example.com
kinit admin
ipa-getcert request -r -f /etc/httpd/httpd-certs/http.crt -k /etc/httpd/httpd-certs/http.key -N CN=webmail.example.com -D webmail.example.com -K http/webmail.example.com
vi /etc/httpd/conf.d/ssl.conf
DocumentRoot "/var/www/html"
ServerName webmail.example.com:443
SSLCertificateFile /etc/httpd/httpd-certs/http.crt
SSLCertificateKeyFile /etc/httpd/httpd-certs/http.key Debian/Ubuntu
Obtain Certs
a2enmod ssl
a2ensite default-ssl
service apache2 reload
mkdir /etc/apache2/ssl
openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/apache2/ssl/apache.key -out /etc/apache2/ssl/apache.crt
chmod 600 /etc/apache2/ssl/*Web App
vi /etc/apache2/sites-enabled/default-ssl.conf
ServerAdmin webmaster@localhost
ServerName example.com:443
DocumentRoot /var/www/html
SSLEngine on
SSLCertificateFile /etc/apache2/ssl/apache.crt
SSLCertificateKeyFile /etc/apache2/ssl/apache.key
service apache2 reloadUncomment the mod_rewrite.so line in /etc/httpd/conf/httpd.conf, restart apache
Try this:In httpd.conf, search for AllowOveride None and change to AllowOveride All, then restart apache
Postfix
Configuration
vi /etc/postfix/main.cf
smtpd_use_tls=yes
#seperate files
smtpd_tls_cert_file=/etc/ssl/certs/certificate.crt
smtpd_tls_key_file=/etc/ssl/private/yourdomainname.key
#single file
smtpd_tls_cert_file=/etc/ssl/certs/certificate_and_key.crt
smtpd_tls_key_file=$smtpd_tls_cert_file
vi /etc/postfix/master.cf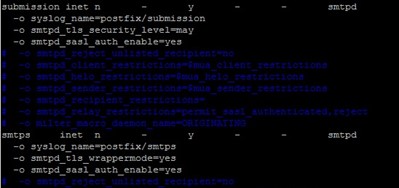
Start Postfix
systemctl restart postfix
telnet localhost 465
#test encryption
echo | openssl s_client -starttls smtp -connect localhost:25 -cipher "EDH" 2>/dev/null | grep -i -e "Server .* key"Dovecot
Configuration
vi /etc/dovecot/conf.d/10-ssl.conf #you can also disable the plaintext auth that we set up in the beginning if you want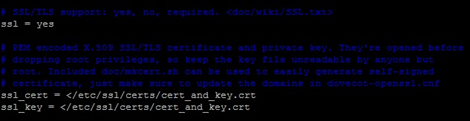
Restart
systemctl restart dovecot
telnet localhost 995/993Links
https://www.rosehosting.com/blog/how-to-generate-a-self-signed-ssl-certificate-on-linux/
──────────────────────────────────────────────────────────────────────────────────
Postfix Auth Integrated w/ Dovecot SASL
Links
https://www.howtoforge.com/postfix-smtp-authentication-on-the-secure-port-only https://www.vennedey.net/resources/2-LDAP-managed-mail-server-with-Postfix-and-Dovecot-for-multiple-domains#sasl_authentication https://doc.dovecot.org/configuration_manual/howto/postfix_and_dovecot_sasl/
Configuration
#Test if Postfix is compatible
postconf -a
#Dovecot Integration
vi /etc/dovecot/conf.d/10-master.conf
service auth {
unix_listener /var/spool/postfix/private/auth {
mode = 0660
user = postfix
group = postfix
}
}
vi /etc/dovecot/conf.d/10-auth.conf
# Outlook and Windows Mail works only with LOGIN mechanism, not the standard PLAIN:
auth_mechanisms = plain login
systemctl restart dovecotPostfix Configuration
Note: this will configure AUTH on port 25
vi /etc/postfix/main.cf
#Add to bottom
smtpd_sasl_type = dovecot
smtpd_sasl_path = private/auth
# On Debian Wheezy path must be relative and queue_directory defined
#queue_directory = /var/spool/postfix
smtpd_sasl_auth_enable = yes
# With Postfix version before 2.10, use smtpd_recipient_restrictions
smtpd_relay_restrictions = permit_mynetworks, permit_sasl_authenticated, reject_unauth_destination
systemctl restart postfixW/ SSL
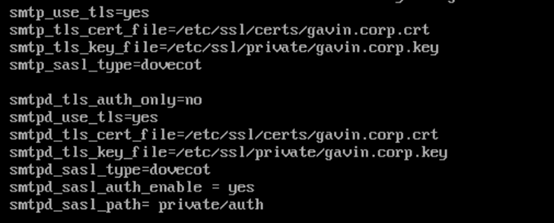
Example Logs
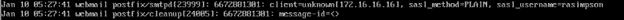
──────────────────────────────────────────────────────────────────────────────────
Conclusion
We have configured some of the common types of authentication mechanisms for our email server. Whatever you choose to implement in your lab, hopefully it works out well! SSL Certs can also be tricky sometimes, but having this skill is important for an increasingly interconnected world to protect the integrity of our information. Happy learning!
