Setting Up Free IPA
──────────────────────────────────────────────────────────────────────────────────
Introduction
FreeIPA is an open-source identity provider for Linux and Unix environments. It is a combination of 389 Directory Server, MIT Kerberos, NTP, DNS, Dogtag, SSSD, and other components. FreeIPA is a great tool for managing users, groups, and hosts in a lab environment. In this post, we will be going over how to set up FreeIPA on a CentOS 8 machine.
Prerequisites
- A Machine that actually supports FreeIPA
- Debian 11 Unstable Package
- Fedora 21
- [...]
- Set hostname to “ipa”
- hostnamectl set-hostname ipa.example.com && reboot
- Static ip address
- /etc/sysconfig/network-scripts/ifcfg-eth0
- Drop your firewall, or add the exceptions to follow
- Add Network Devices to Hosts File
- echo “
ipa.example.com ipa” >> /etc/hosts - echo “
www.example.com www” >> /etc/hosts - Fix DNS Resolve
- echo nameserver 1.1.1.1 >> /etc/resolv.conf
- echo nameserver 8.8.8.8 >> /etc/resolv.conf
- Double Check
- hostname -f && hostname -s && hostname -d
Firewall Rules
| Service | Protocol | Ports |
|---|---|---|
| HTTP/S | TCP | 80, 443 |
| LDAP/S | TCP | 389, 636 |
| Kerberos | TCP & UDP | 88, 464 |
| DNS | TCP & UDP | 53 |
| NTP | UDP | 123 |
| Dogtag Cert System - LDAP | TCP | 7389 |
──────────────────────────────────────────────────────────────────────────────────
Installation
First, we will install the necessary packages for FreeIPA. We will also remove the bind-chroot package as it is not needed for our purposes.
#install packages
yum -y install freeipa-server bind bind-dyndb-ldap && yum remove bind-chroot
#install IPA
ipa-server-install --ssh-trust-dns --setup-dns --idstart=50000 --idmax=99999 --mkhomedir
After the installation, we will need to restart the sshd service and then log in as the admin user. We will then verify that the admin user exists and then modify the DNS forwarders to use Google’s DNS servers. We will also need to modify the nsswitch.conf file to include the sudoers file.
#post installation tasks
systemctl restart sshd
kinit admin
ipa user-find admin
ipa dnsconfig-mod --forwarder=1.1.1.1 --forwarder=8.8.8.8
echo “sudoers: files sss” >> /etc/nsswitch.conf
vi /etc/sssd/sssd.conf
services = nss, pam, ssh, sudo
──────────────────────────────────────────────────────────────────────────────────
Usage - Command Line-Fu
Adding DNS Records
#new dns record - fill in prompts manually
ipa dnsrecord-add
#new dns record - loaded
ipa dnsrecord-add --name=”webmail” --zone=”frog.com” --type=”A”
Adding Hosts
#add new host to IPA
ipa host-add
Adding Services
#**in order to get a keytab for neato SSL/TLS **
#add service - prompt
ipa service-add
#add service - no prompt
ipa service-add smtp/www.example.com
Creating Users
#add user - normal prompt
ipa user-add --password
#add user - with extra args
ipa user-add --first= --last= --password
#**IPA prompts to change the user’s password on initial login FYI**
Scripted Version
vi ipausers.sh
#!/bin/bash
for i in {1..200}
do
username=$(cat /dev/urandom | tr -dc ‘a-z’ | fold -w 8 | head -n 1) #creates 200 random users
#password=”yourinitialpass”
password=$(cat /dev/urandom | tr -dc ‘a-zA-Z0-9’ | fold -w 12 | head -n 1) #random passwords
echo “$username:$password” >> userinfo.txt #so you can reference this later
echo -e “$password\n$password” | ipa user-add $username --first=$username --last=$username --password
echo -e “$password\n$password\n$password” | kinit $username #logs in and keeps same pwd
done
Enable/Disable User
#enable user
ipa user-enable
#disable user
ipa user-disable
Change User Password
ipa user-mod --password
Password Policy
#Show
ipa pwpolicy-show
ipa pwpolicy-show --user=test
#modify
ipa pwpolicy-mod {flags}
{flags}
--minlife=7
--maxlife=90
--history=3
--minlength=6
--maxlength=12
Groups
#add a new group
ipa group-add
#add user to group
ipa group-add-member --users={}
#add group to group
ipa group-add-member --groups={}
#remove users from group
ipa group-remove-member --users=test3
#show members
ipa group-show
#delete a group
ipa group-del
Certs
#log into ipa server
kinit admin
# add host
ipa host-add host.example.com
# add service
ipa service-add HTTP/host.example.com
# ipa server to manage cert
ipa service-add-host --hosts=ipa.example.com HTTP/host.example.com
#new cert
ipa-getcert request -r -f /etc/pki/tls/certs/host.example.com.crt -k /etc/pki/tls/private/host.example.com.key -N CN=host.example.com -D host.example.com -K HTTP/host.example.com
#copy cert and key
rsync -P /etc/pki/tls/certs/host.example.com.crt /etc/pki/tls/private/host.example.com.key
HBAC Rules
#Create rule:
ipa hbacrule-add sshd-ipa
#Add a user to the rule:
ipa hbacrule-add-user --users=ttester sshd-ipa
#Add a host group to the rule:
ipa hbacrule-add-host --hostgroups=ipa sshd-ipa
#Add a service to the rule:
ipa hbacrule-add-service --hbacsvcs=sshd sshd-ipa
#Verify:
ipa hbacrule-show sshd-ipa
ssh test@localhost
#Example - Allow ALL
ipa hostgroup-add allow_all_hosts
ipa host-find --raw --pkey-only --sizelimit=0 | awk '$1 == "fqdn:" { print "--hosts=" $2 }' | xargs -n100 ipa hostgroup-add-member allow_all_hosts
ipa hbacrule-add allow_all_users_services --usercat=all --servicecat=all
ipa hbacrule-add-host allow_all_users_services --hostgroups=allow_all_hosts
#Example - Allow SSH
ipa hbasvc-add sshd
ipa hbacrule-add allow_sshd
ipa hbacrule-add-service allow_sshd --hbacsvcs=sshd
ipa hbacrule-add-user allow_sshd --hosts=workstation.example.com
ipa hbacrule-add-user allow_sshd --user=linuxadmin
ipa hbactest --user=linuxadmin --host=workstation.example.com --service=sshd
#On the Host Machine:
vi /etc/pam.d/sshd
auth required pam_sss.so
account required pam_sss.so
──────────────────────────────────────────────────────────────────────────────────
Client Configuration
Adding DNS Records on IPA Server
ipa dnsrecord-add --name=”host” --zone=”example.com” --type=”A”
Add Email Server to IPA Server
ipa host-add www.example.com
Verify content of /etc/hosts
(should have your ip - hostname mapping at a minimum)
vi /etc/hosts
Install FreeIPA Client
yum -y install ipa-client-install
Verify
kinit admin
klist
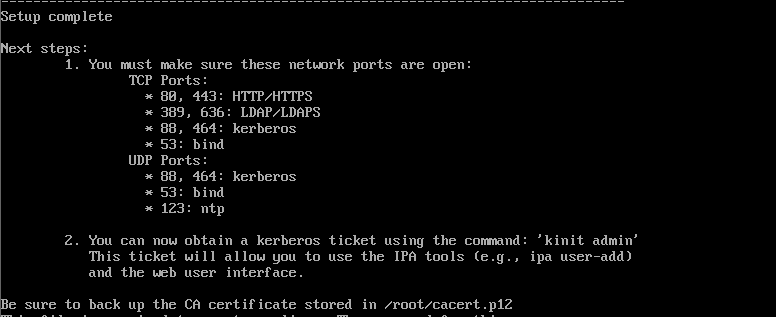
If everything goes as expected, you should get a prompt that looks like the following:
──────────────────────────────────────────────────────────────────────────────────
OpenSuse
#Get Keytab Auth
#From IPA Server >>
/usr/sbin/ipa-getkeytab -s ipa.example.com -p host/suse.example.com -k /tmp/suse.keytab
scp /tmp/suse.keytab suse.example.com:/tmp/krb5.keytab
#From IPA Client >>
cp /tmp/krb5.keytab /etc
chmod 600 /etc/krb5.keytab
mkdir /etc/ipa
curl -o /etc/ipa/ca.crt http://ipa.example.com/ipa/config/ca.crt
curl -o /etc/pki/trust/anchors/ipa.example.com.crt http://ipa.example.com/ipa/config/ca.crt
update-ca-certificates
zypper install sssd sssd-ipa yast2-auth-client krb5-client openldap2-client cyrus-sasl-gssapi
# Setup SSSD
vi /etc/sssd/sssd.conf
[domain/example.com]
cache_credentials = True
krb5_store_password_if_offline = True
ipa_domain = example.com
ipa_hostname = suse.example.com
ipa_server = _srv_, ipa.example.com
dns_discovery_domain = example.com
id_provider = ipa
auth_provider = ipa
access_provider = ipa
chpass_provider = ipa
ldap_tls_cacert = /etc/ipa/ca.crt
[sssd]
services = nss, sudo, pam, ssh
domains = example.com
[nss]
filter_users = root,ldap,named,avahi,haldaemon,dbus,radiusd,news,nscd,tomcat,postgres
homedir_substring = /home
[pam]
[sudo]
[autofs]
[ssh]
# Setup Kerberos
vi /etc/krb5.conf
[libdefaults]
default_realm = EXAMPLE.COM
dns_lookup_realm = true
dns_lookup_kdc = true
rdns = false
dns_canonicalize_hostname = false
ticket_lifetime = 24h
forwardable = true
udp_preference_limit = 0
default_ccache_name = KEYRING:persistent:%{uid}
[realms]
EXAMPLE.COM = {
pkinit_anchors = FILE:/var/lib/ipa-client/pki/kdc-ca-bundle.pem
pkinit_pool = FILE:/var/lib/ipa-client/pki/ca-bundle.pem
}
[domain_realm]
.example.com = EXAMPLE.COM
example.com = EXAMPLE.COM
suse.example.com = EXAMPLE.COM
# Setup pam
pam-config -a --sss --mkhomedir --mkhomedir-umask=0077 --pwhistory --pwhistory-remember=5 --localuser --cracklib --cracklib-minlen=14 --cracklib-dcredit=-1 --cracklib-ucredit=-1 --cracklib-lcredit=-1 --cracklib-ocredit=-1 --cracklib-retry=3 --unix-sha512
# Setup nsswitch
sed -i.bak 's/compat$/files sss/g' /etc/nsswitch.conf
echo "sudoers: files sss" >> /etc/nsswitch.conf
sed -i '/netgroup/ s/nis/sss/g' /etc/nsswitch.conf
#Set NIS Domain Name
sed -i.bak '/NETCONFIG_NIS_STATIC_DOMAIN/ s/""/"example.com"/g' /etc/sysconfig/network/config
netconfig update -f
# Start sssd
systemctl enable sssd --now
# Verify
id admin
──────────────────────────────────────────────────────────────────────────────────
Centos 8 / RHEL 8
yum module list idm
yum module info idm:client
yum -y install @idm:client
rpm -qi ipa-client && rpm -qi sssd
echo "192.168.58.121 ipa.example.com"| sudo tee /etc/hosts
export HNAME="host.example.com"
hostnamectl set-hostname $HNAME --static
hostname $HNAME
ipa-client-install --hostname=host.example.com --mkhomedir --server=ipa.example.com --domain example.com --realm EXAMPLE.COM
ipa-client-install
authconfig --enablemkhomedir --update
──────────────────────────────────────────────────────────────────────────────────
Service Configuration
Dovecot - IMAP
# 1. Add Service to IPA Server
ipa service-add imap/www.example.com
# 2. Add Mail Group
ipa group-add mailusers
ipa group-add-member mailusers --users={test1,test2,test3}
# 3. Configure IPA Client
#ref client config
# 4. Basic Dovecot Install
yum -y install dovecot
systemctl enable dovecot
# 5. Configure to Allow imap
vi /etc/dovecot/dovecot.conf
protocols = imap
# 6. Kerberos Authentication
vi /etc/dovecot/conf.d/10-auth.conf
auth_mechanisms = gssapi
auth_gssapi_hostname = webmail.example.com
auth_krb5_keytab = /etc/dovecot/krb5.keytab
auth_realms = example.com
auth_default_realm = example.com
userdb {
driver = static
args = uid=dovecot gid=dovecot home=/var/spool/mail/%u
}
# 7. Configure Mailbox Location
vi /etc/dovecot/conf.d/10-mail.conf
mail_location = maildir:~/Maildir
# 8. Start Dovecot
systemctl start dovecot
──────────────────────────────────────────────────────────────────────────────────
Postfix - SMTP
# 1. Add Service to IPA Server
ipa service-add smtp/www.example.com
# 2. Configure IPA Client - If Not Done Already
#ref client config
# 3. Basic Postfix Install
yum -y install postfix
systemctl enable postfix
# 4. Configure Basic Settings
vi /etc/postfix/main.cf
myhostname = .
mydomain =
myorigin = $mydomain
inet_interfaces = all
mynetworks =
home_mailbox = /var/mail/users
vi /etc/postfix/master.cf
#uncomment:
submission inet n - n - - smtpd
-o syslog_name=postfix/submission
-o smtpd_tls_security_level=encrypt
-o smtpd_sasl_auth_enable=yes
# 5. LDAP Mappings
postconf -e ‘virtual_alias_domains = example.com’
postconf -e ‘virtual_alias_maps = ldap:/etc/postfix/ldap_aliases.cf’
vi /etcpostfix/ldap_aliases.cf
server_host = ipa.example.com
search_base = cn=accounts,dc=example,dc=com
query_filter = (mail=%s)
result_attribute = uid
bind = no
start_tls = yes
version = 3
postmap /etc/postfix/ldap_aliases.cf
restorecon -R /etc/postfix/
systemctl restart postfix
# 6. SASL (Single Sign on for Authentication) Config
yum -y install cyprus_sasl
kinit admin
ipa-getkeytab -s ipa.example.com -p smtp/webmail.example.com -k /etc/postfix/smtp.keytab
chown root:mail /etc/postfix/smtp.keytab
chmod 640 /etc/postfix/smtp.keytab
vi /etc/sasl2/smtpd.conf
pwcheck_method: saslauthd
mech_list: GSSAPI PLAIN LOGIN
vi /etc/sysconfig/saslauthd
SOCKETDIR=/var/run/saslauthd
MECH=kerberos5
FLAGS=
postconf -e 'import_environment = MAIL_CONFIG MAIL_DEBUG MAIL_LOGTAG TZ XAUTHORITY DISPLAY LANG=C KRB5_KTNAME=/etc/postfix/smtp.keytab'
postconf -e 'smtpd_client_restrictions = permit_sasl_authenticated, reject'
postconf -e 'smtpd_recipient_restrictions = permit_sasl_authenticated, reject'
postconf -e 'smtpd_sender_restrictions = permit_sasl_authenticated, reject'
postconf -e 'smtpd_sasl_auth_enable = yes'
postconf -e 'smtpd_sasl_security_options = noanonymous'
postconf -e 'smtpd_sasl_tls_security_options = $smtpd_sasl_security_options'
postconf -e 'broken_sasl_auth_clients = yes'
postconf -e 'smtpd_sasl_authenticated_header = yes'
postconf -e 'smtpd_sasl_local_domain = $mydomain'
systemctl enable saslauthd
systemctl restart saslauthd
systemctl restart postfix
# 7. TLS Connections
mkdir /etc/postfix-certs
chcon -t cert_t /etc/postfix-certs
ipa-getcert request -r -f /etc/postfix-certs/smtp.crt -k /etc/postfix-certs/smtp.key -N CN=webmail.example.com -D webmail.example.com -K smtp/webmail.example.com
postconf -e 'smtpd_tls_auth_only = yes'
postconf -e 'smtpd_tls_key_file = /etc/postfix-certs/smtp.key'
postconf -e 'smtpd_tls_cert_file = /etc/postfix-certs/smtp.crt'
postconf -e 'smtpd_tls_received_header = yes'
postconf -e 'smtpd_tls_session_cache_timeout = 3600s'
systemctl restart postfix
──────────────────────────────────────────────────────────────────────────────────
HTTP LDAP Login Page
# 11. Add Webserver to IPA Server
ipa host-add www.example.com
# 12. Add Service to IPA Server
ipa service-add HTTP/www.example.com
# 13. Configure IPA Client
#ref client config
# 14. Install
yum -y install mod_ldap mod_auth_kerb
# 15. Get Keytab
kinit admin
ipa-getkeytab -s ipa.www.example.com -p ipa-getkeytab -s ipa.www.example.com -p HTTP/www.example.com -k /etc/httpd/conf.dkeytab
chwon apache:apache /etc/httpd/conf.d/keytab
vi /etc/httpd/conf.d/auth_ipa.conf #new file
SSLRequireSSL
AuthName "IPA Authentication"
AuthType Kerberos
KrbServiceName HTTP
KrbMethodK5Passwd On
KrbSaveCredentials On
KrbMethodNegotiate On
KrbAuthRealms EXAMPLE>COM
Krb5KeyTab /etc/httpd/conf.d/keytab
AuthLDAPUrl ldap://<>/dc=example,dc=com?krbPrincipalName
Require valid-user
systemctl restart httpd
# 16. Test
vi /var/www/html/ipa/index.html
<html>
<body>
<div style="width: 100%; font-size: 40px; font-weight: bold; text-align: center;">
Test Page for IPA Server Auth </div>
</body>
</html>
──────────────────────────────────────────────────────────────────────────────────
References
- Fedora FreeIPA Guide
- FreeIPA HBAC Allow All
- Linux Guide and Hints - FreeIPA
- https://www.dalemacartney.com/2013/03/14/deploying-postfix-with-ldap-freeipa-virtual-aliases-and-kerberos-authentication
- https://www.dalemacartney.com/2012/07/05/configuring-dovecot-to-authenticate-freeipa-users-using-kerberos-with-single-sign-on
- Debian Postfix and SASL
──────────────────────────────────────────────────────────────────────────────────
Conclusion
FreeIPA is a great tool for managing users, groups, and hosts in a lab environment. It is a great way to learn about identity management and LDAP. It is also a great way to learn about the different services that are used in a Linux environment. I hope this post has been helpful and informative. If you have any questions or comments, please feel free to reach out to me.
